Cisco Integration Certificate Enrollment loop issue
Issue
An issue was detected in which users encounter a certificate loop during the certificate enrollment process.
Background Information
Users get the requested certificate, but when they connect they are taken through the enrollment process again. This scenario usually occurs for IE 8 users.
Troubleshooting
Certificate loops are usually caused by one of a few things
Clock is off: When a certificate is issued it has an Issued Date and an Expiry Date. If the clock on the ASA is slow (or the time zone is off) a newly issued certificate may not seem to be "yet" valid (i.e. it is 8 a.m. and the user receives a new certificate, but the ASA thinks it is 2 a.m. the ASA will not 'think' the certificate is valid for another 6 hours).
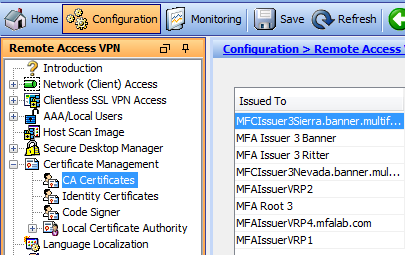
Certificate validation error: The personal certificate for which the user enrolls is cryptographically signed by a Certificate Authority (CA). The ASA must have the CA certificates imported to the CA store in order to validate the signature on the personal certificate.
Here is a snip of ASDM showing the CA certs:
 |
ASDM Log Information
ASDM logs provide information about the CA certificates. On a busy ASA, log feeds flow too quickly to be of much use, but there are settings to help us make the ASDM log viewer useful.
How to configure filters for ASDM logs
Under Configuration > Device Management > Logging > Logging Filters select the type of ASDM messages to show. Notice logging filters can be configured separately for each type of logging. When logs are filtered in ASDM for troubleshooting, the audit trail that is compiling in a Syslog Server remains undamaged.
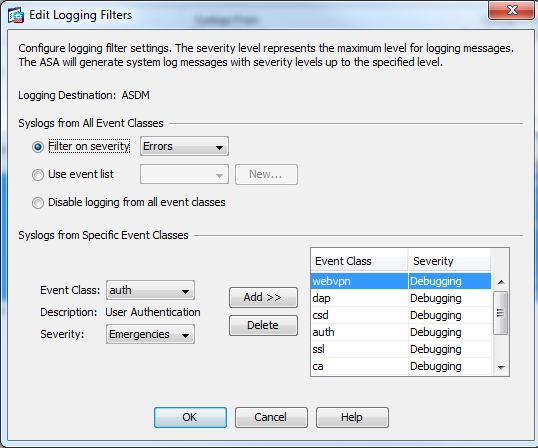
The image below shows that the overall severity of messages in the ASDM log viewer is restricted to 'Errors'. The bottom section of the window permits selection of specific event classes, and the class level to be logged. In this scenario, classes useful for certificate, authentication and connection troubleshooting are selected. To the right of the snip is a complete list of categories that are typically helpful.
 |
What information is needed from ASDM logs
The following information needs to be verified in the ASDM logs:
the certificate is validated
the Tunnel-Group-Map placed the user in the appropriate Profile
A successful certificate validation and mapping shows the following lines of information:
identified client certificate
This indicates the ASA has received a certificate from the user
looking for a tunnel group match
Tunnel group match found
This message indicates the valid certificate:
matched a map
delivered the user to a profile that requires cert+AAA
is configured to grant access to the protected resources or network
The message also provides information that indicates to which Profile/tunnel-group the session was mapped
The logs also include error messages that might provide insight into this issue. For example, there might be messages about the certificate date being out of range – either expired, or, as described above, if the ASA clock is slow. Or the tunnel-group match found message might appear, indicating certificates are not mapping adequately. This scenario might prompt an investigation to examine the content of the certificate, and the configured certificate map to the profile, to figure out why they do not match.