OTP Troubleshooting
Introduction
This article discusses basic troubleshooting techniques for resolving issues with the One Time Password (OTP) functionality in SecureAuth IdP.
Applies to
SecureAuth IdP Version | OS Version |
|---|---|
7.x+ |
|
SMS and Voice Delivery Issues
Verify the time, time zone, and date are correct on SecureAuth IdP
When an end-user selects the SMS or Voice option to deliver an OTP code, the request is sent to the cloud environment for fulfillment.
SecureAuth IdP appliances use the Windows Communication Foundation (WCF) protocol to ensure secure communications between the appliance and cloud environment. The underlying technologies used by WCF are sensitive to time discrepancies and will fail if the appliance clock is off by five or more minutes. In real world usage, SecureAuth has seen intermittent issues start with a clock drifting off by three minutes.
If the SecureAuth IdP appliance is not joined to the domain, SecureAuth recommends configuring it to use a reliable (S)NTP server to keep the clock disciplined. To verify the time / date on the appliance and, if necessary, configure NTP, refer to the Microsoft support document Set the Clock.
Verify the Web Proxy Server configuration (if applicable)
If a Web Proxy Server is used for communication to the public Internet, ensure the realm is configured correctly.
Refer to the document pertinent to the SecureAuth IdP version for more information about this topic
SecureAuth IdP Version 9.1+ - Web Proxy Server Configuration Guide (version 9.1+)
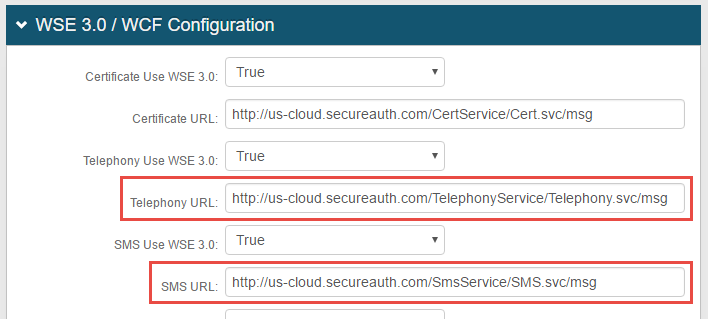
Verify URLs for cloud services are configured correctly
Verify certificates have not expired
Ensure the impacted realms have current, valid certificates selected for communication with the cloud environment
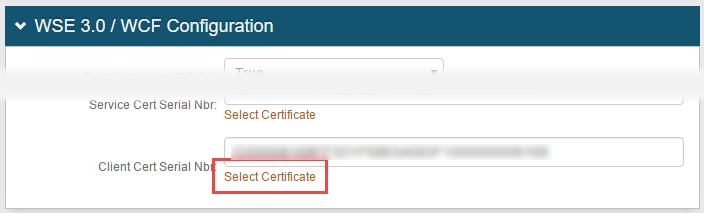
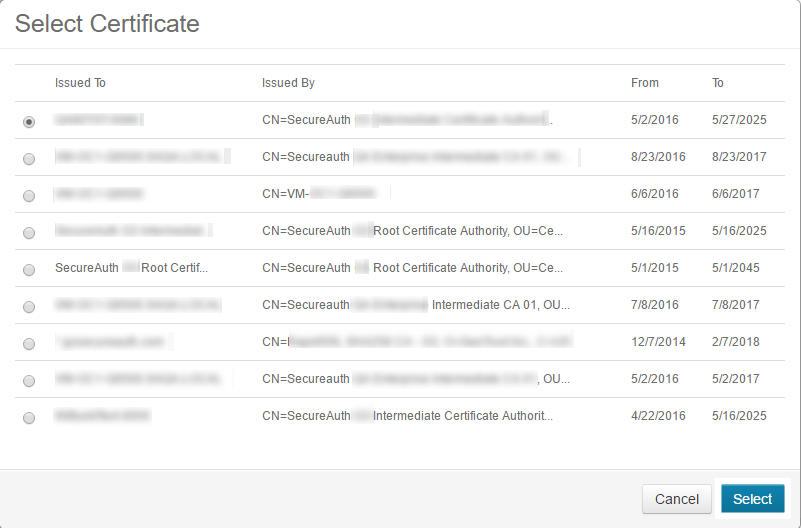
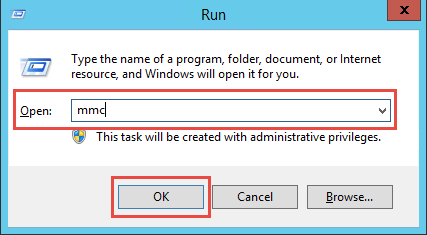
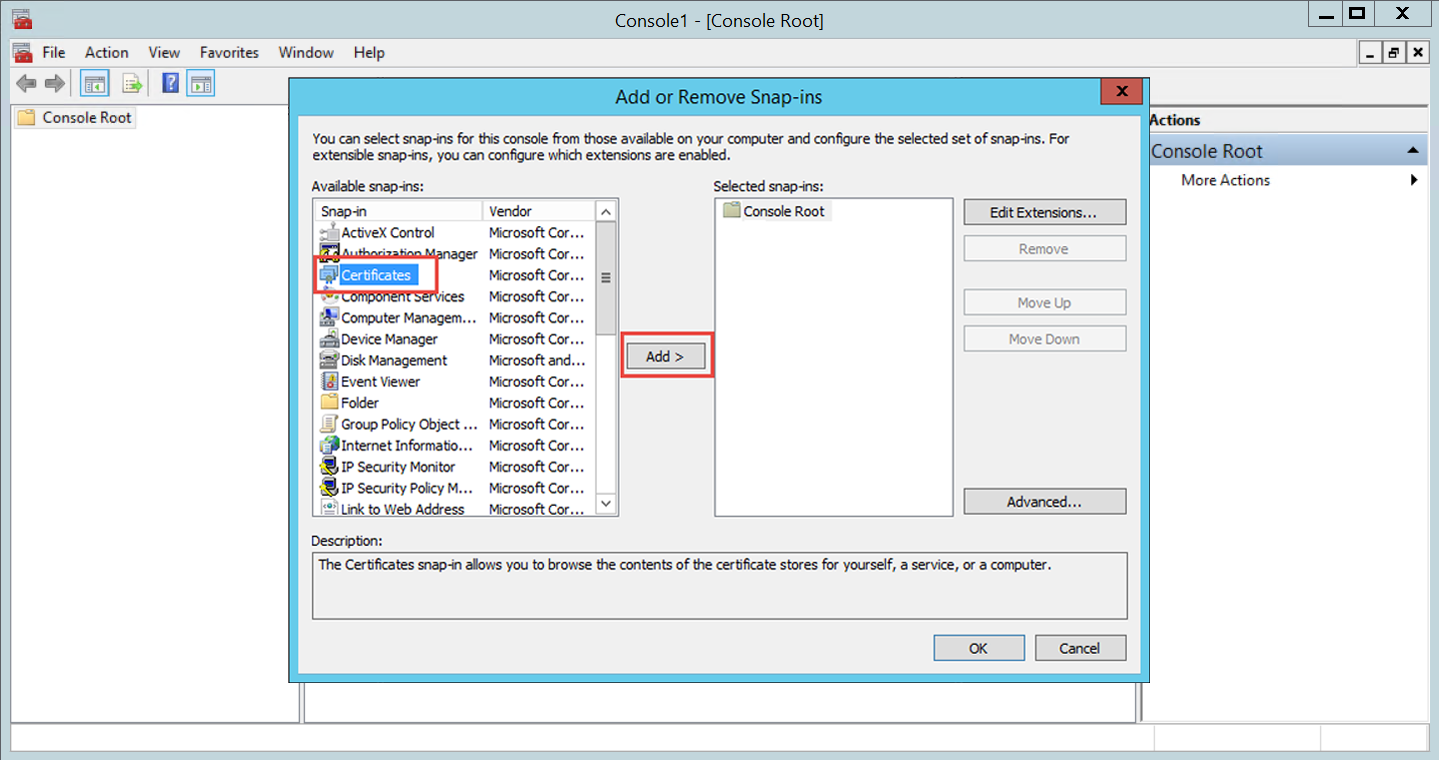
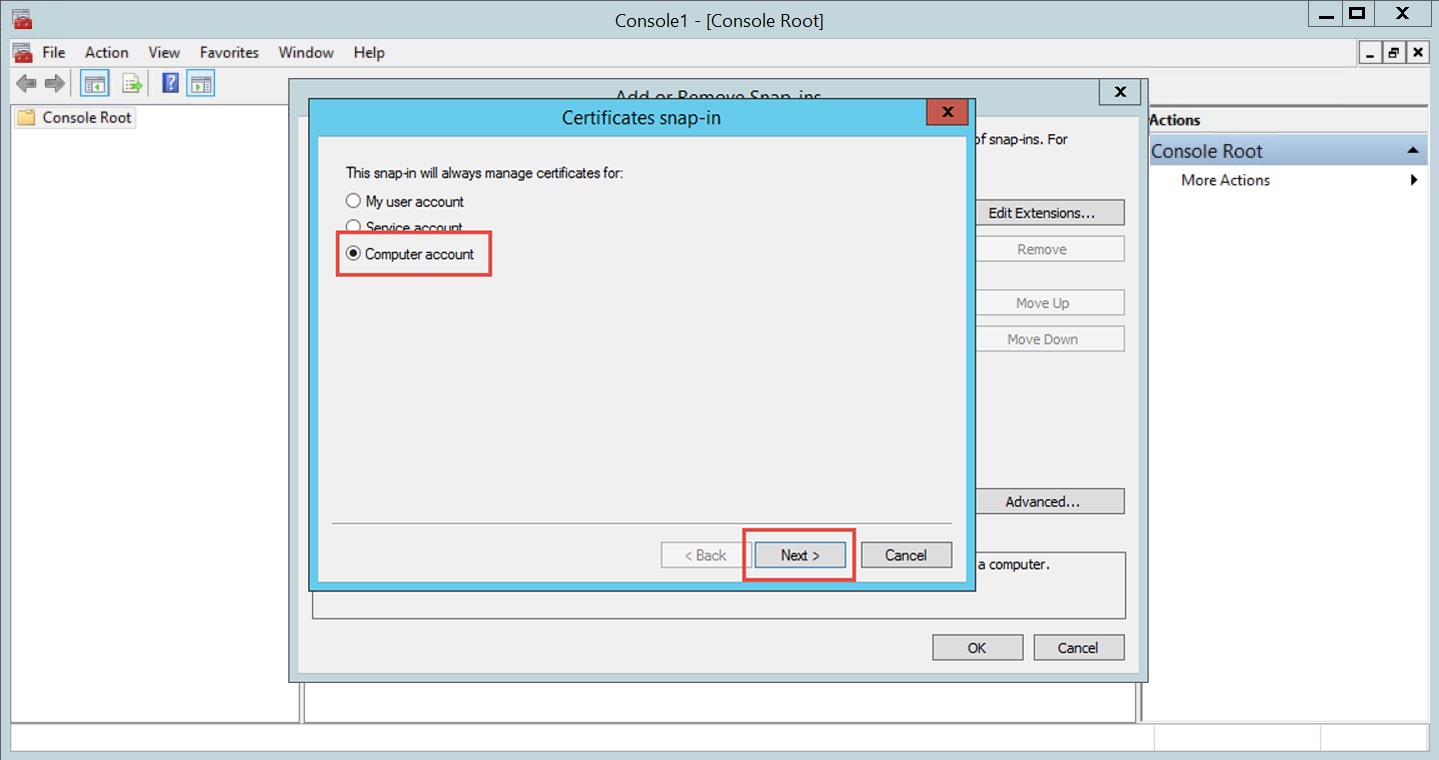
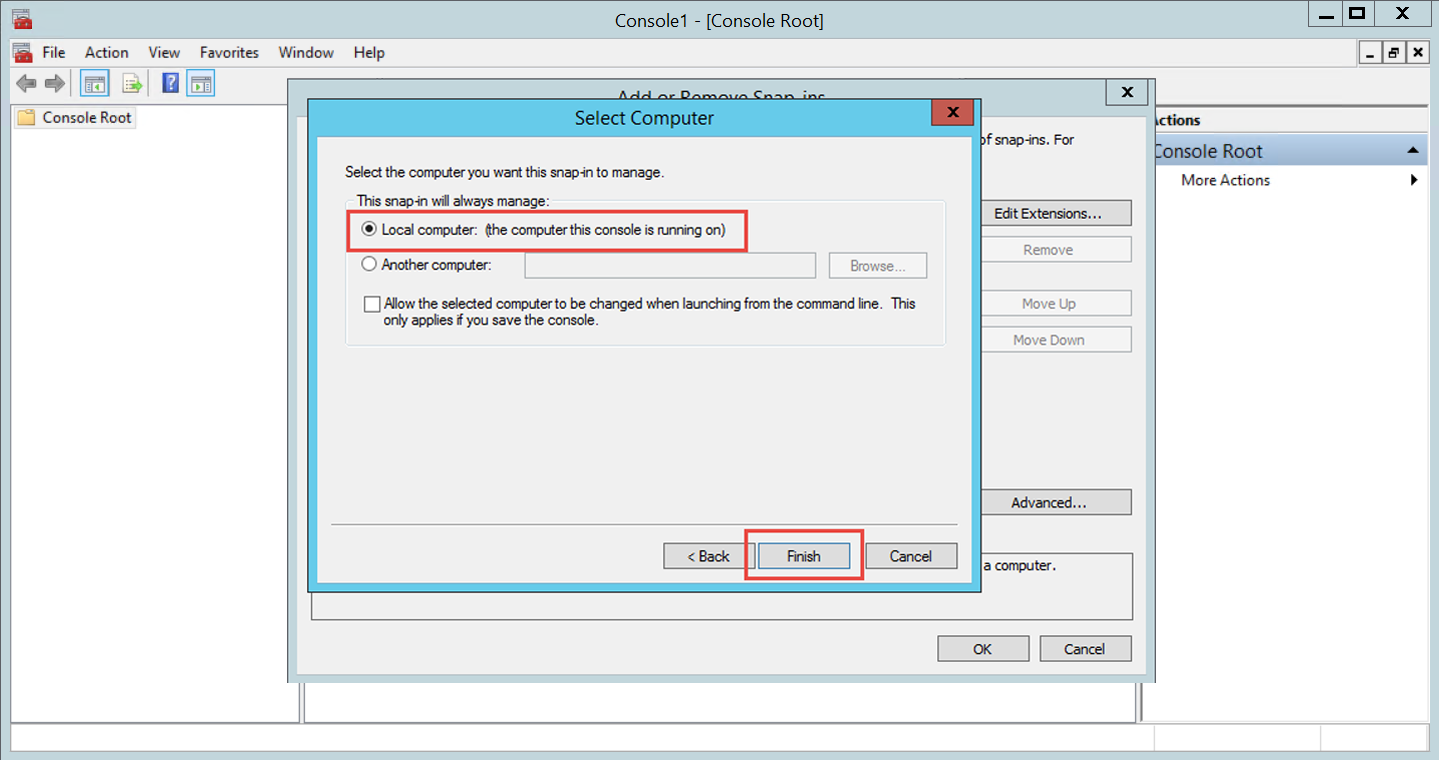
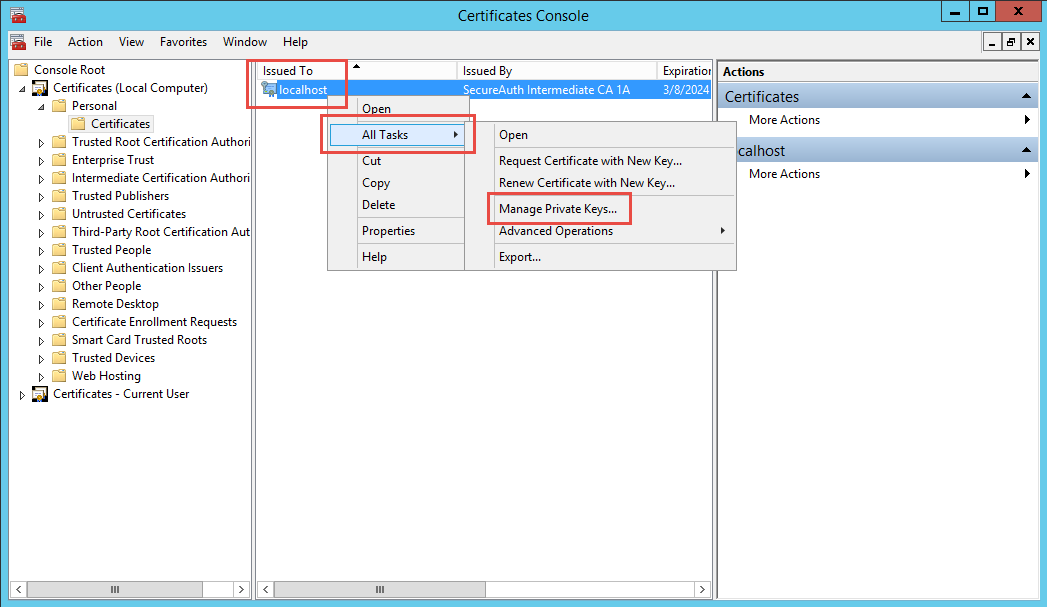
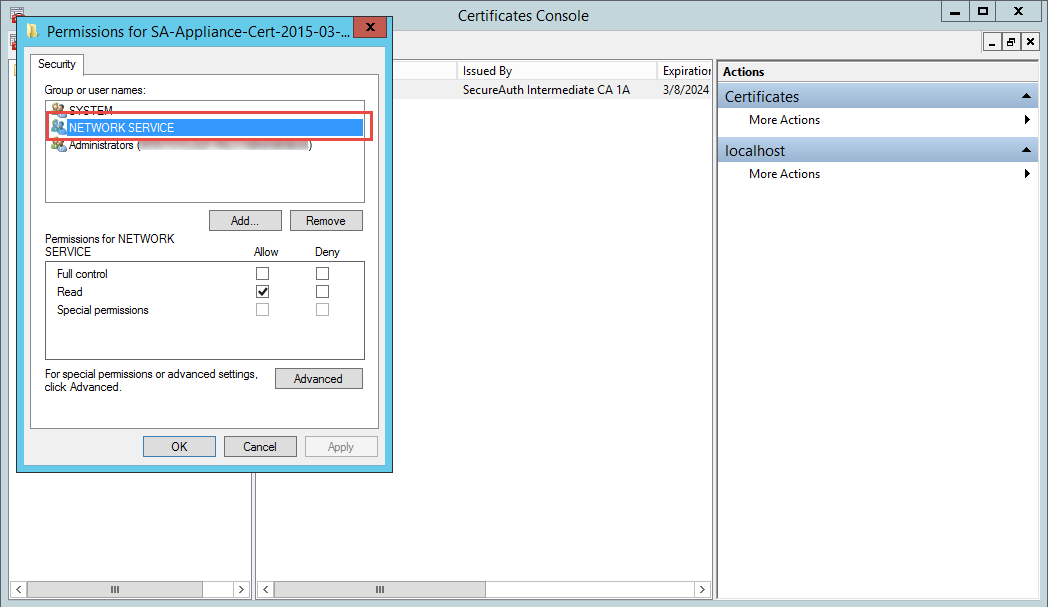
Verify the certificate private key is granted proper privileges
A certificate is used to communicate with the SecureAuth IdP cloud environment. If the certificate's private key is not granted appropriate privileges, then a connection to the cloud infrastructure cannot be made. Without this connectivity, the OTP code cannot be delivered to users via SMS or Voice.
Follow SecureAuth IdP Steps and Microsoft Management Console Steps to ensure the certificate is granted appropriate private key privileges
Verify the support license is current
If the organization's support license is not current, the cloud service will reject any connection attempts, for security purposes
If this is suspected to be an issue, contact the SecureAuth account manager (AM) or SecureAuth Support
Email Delivery Issues
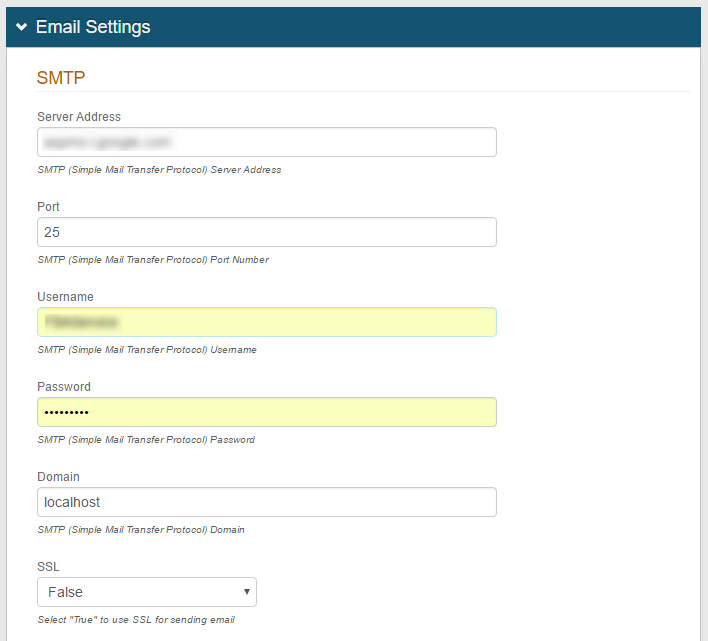
Check the SMTP settings on the impacted realm(s) to verify the proper server is being used
Verify SMTP settings
Verify firewall settings
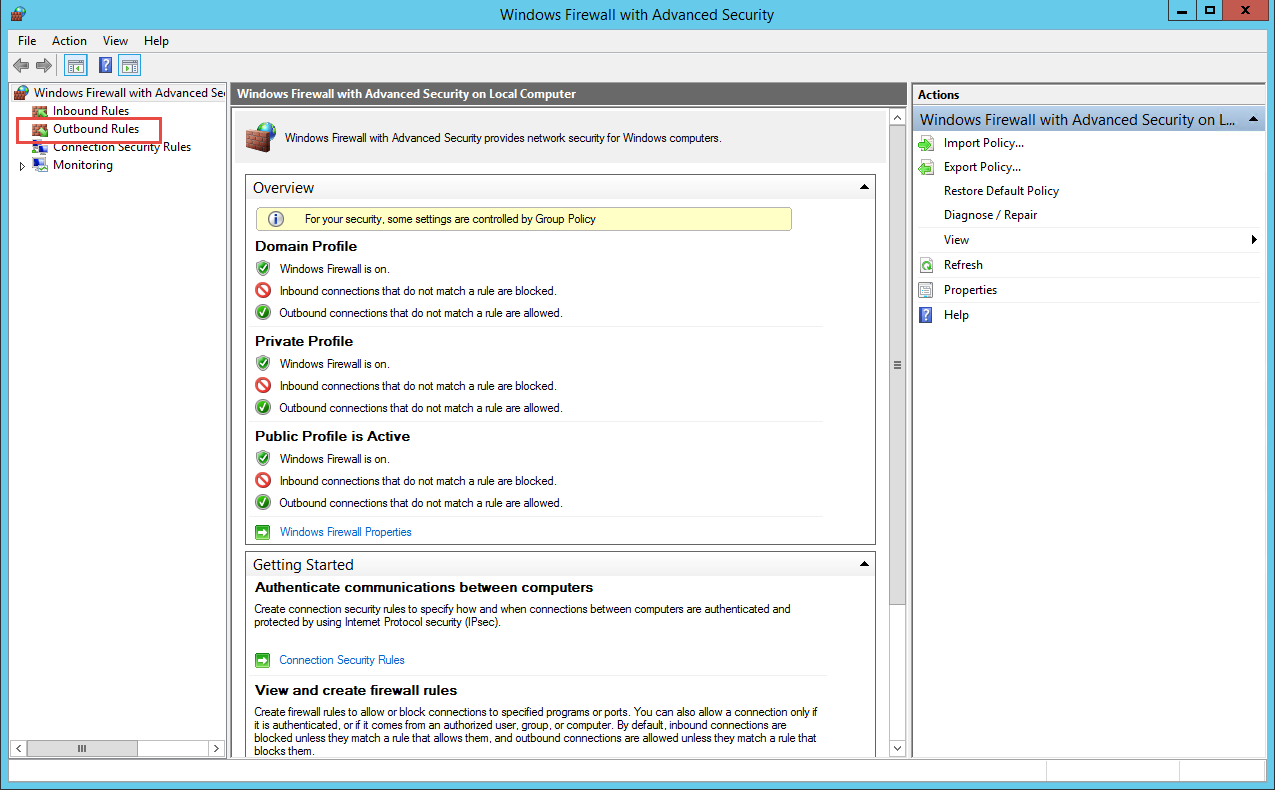
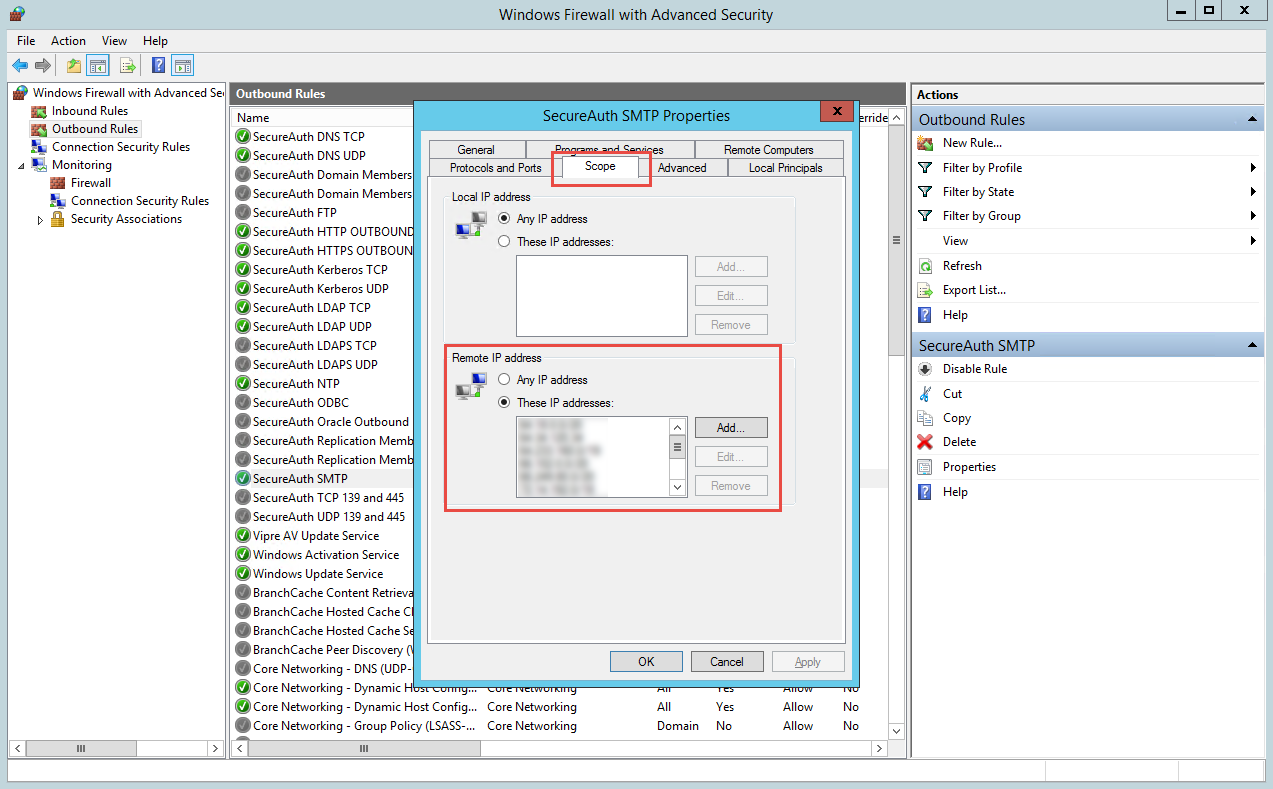
SecureAuth IdP uses the standard Simple Mail Transport Protocol (SMTP) to transmit mail. This communication occurs on TCP / 25 and all firewalls between the SecureAuth IdP appliance and the SMTP server must allow this traffic to pass.
On the SecureAuth IdP appliances, Windows Firewall with Advanced Security includes an outbound policy named SecureAuth SMTP for SMTP traffic. For this policy, the SMTP server IP address must be listed in the Remote IP address section.
Enable SMTP over SSL / TLS (if applicable)
In some cases the SMTP server will require SMTP communication to occur over SSL / TLS
See the technical document Enable SSL/TLS Support for SMTP for further information on how to enable this functionality
OATH Second Factor Issues
Verify the same license certificate is used for all OATH realms
If the SecureAuth998 (provisioning) realm is configured to store the OATH Seed using Advanced Encryption, then all realms using OATH must share the same license certificate
If the same certificate is not used, then the realm will be unable to decrypt the OATH Seed and will fail to authenticate the user
In this scenario, the end-user will normally receive the Registration code does not match error